Microsoft 365 Authentication
This guide will explain how to set up an external login provider connecting to Azure Active Directory (Azure AD) so that it becomes possible for users to login to backend and frontend with Azure AD accounts including Office 365 accounts.
Please note that the Dynamicweb solution must have a valid SSL certificate.
Azure AD setup
To set up external authentication using Azure AD you must first create a tenant. An Azure AD tenant is a sort of directory, in this case a collection of user accounts which you want to give access to a Dynamicweb backend using their regular Office 365 credentials.
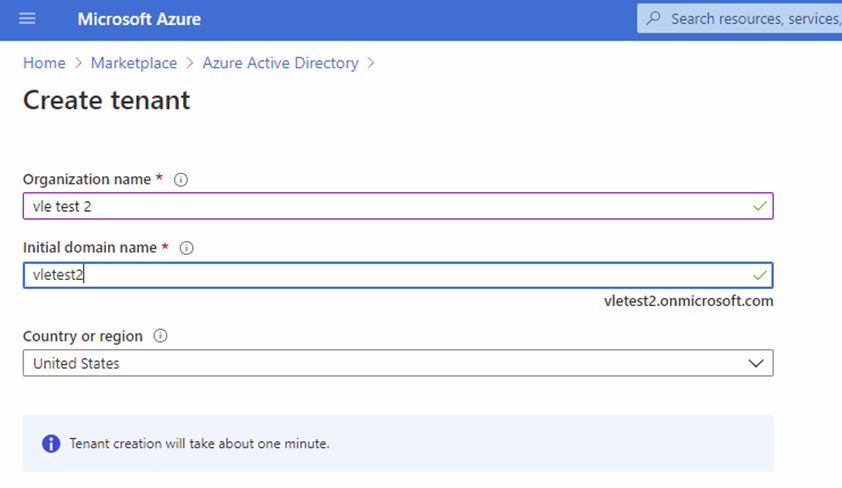
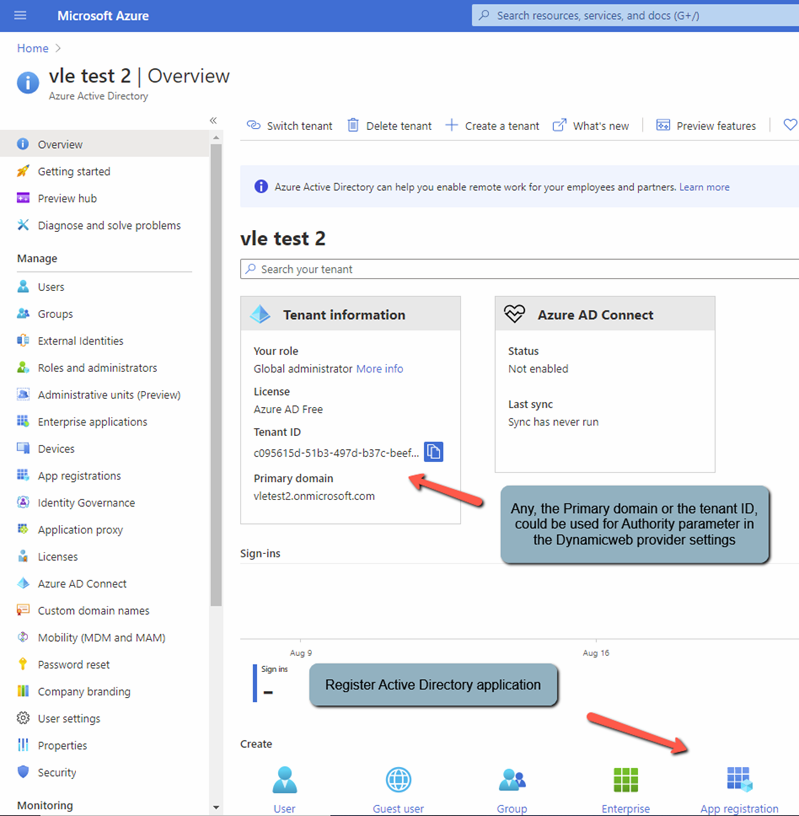
- After the tenant has been created, click Continue to go to the Active directory Overview page. Copy the tenant ID or primary domain and store it somewhere, as you will need it when setting up the Dynamicweb login provider.
- Next register an Application – basically creating an API key for a service to connect to Azure AD. Make sure you select an appropriate account type as you cannot change it later on.
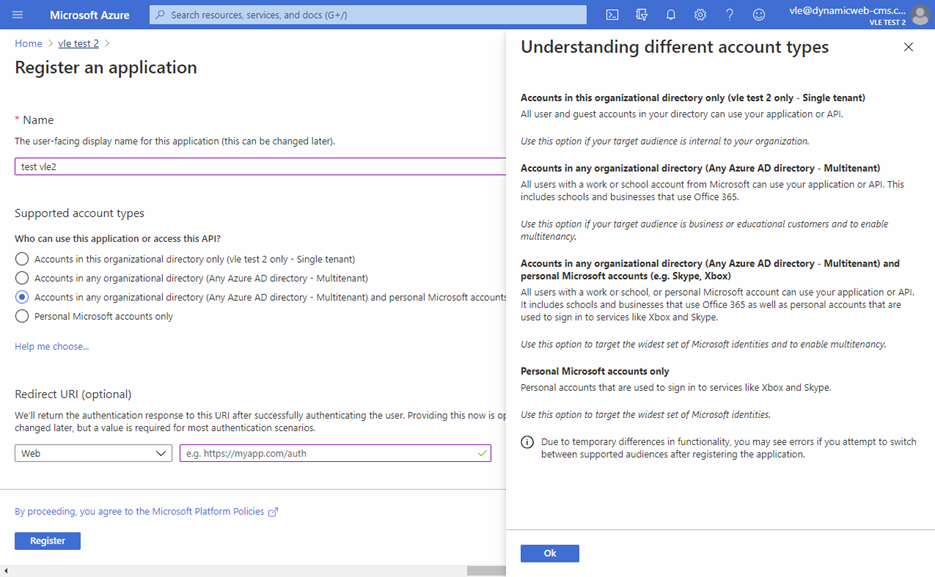
- After the application has been created, you will be navigated to Application Overview page. Copy the Application ID and store it somewhere, as you will need it when setting up the Dynamicweb login provider.
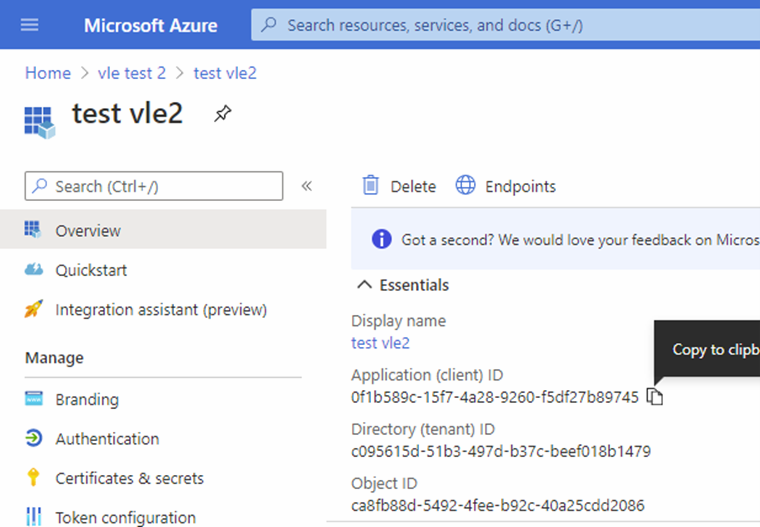
- Now you must set up Authentication:
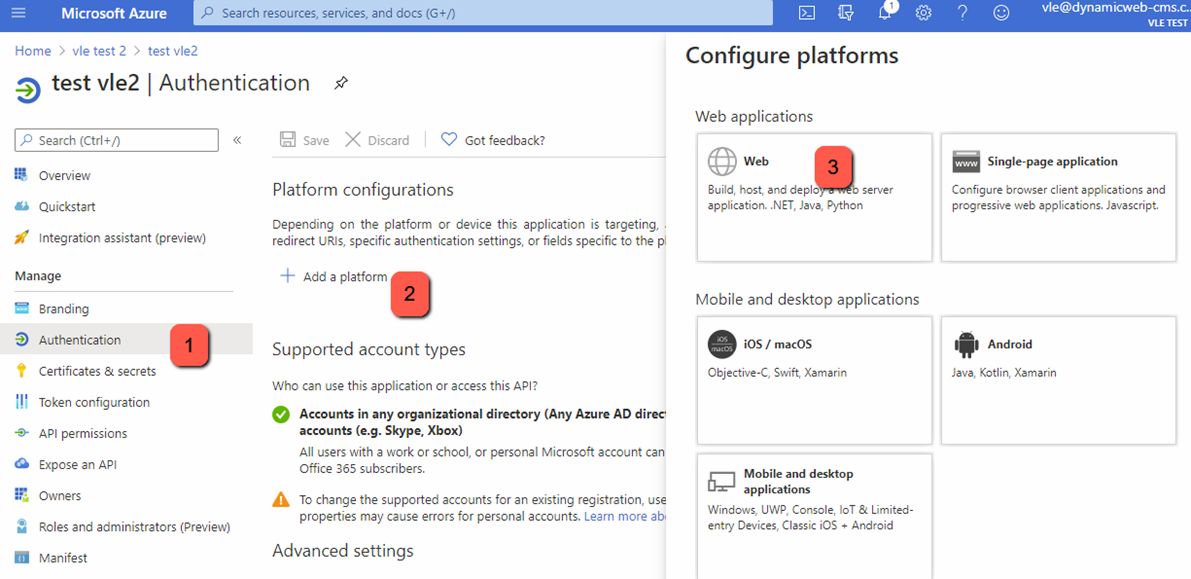
- Click Authentication
- Click Add platform
- Click Web
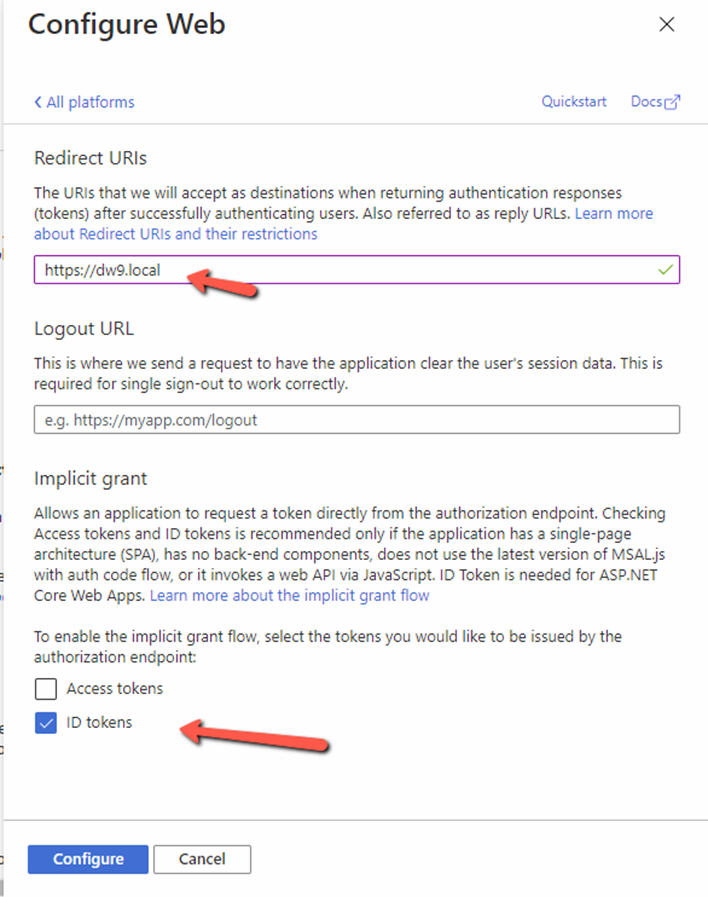
- Enter your solution url – remember it should be https – and select ID tokens as the authorization method (Figure 3.3)
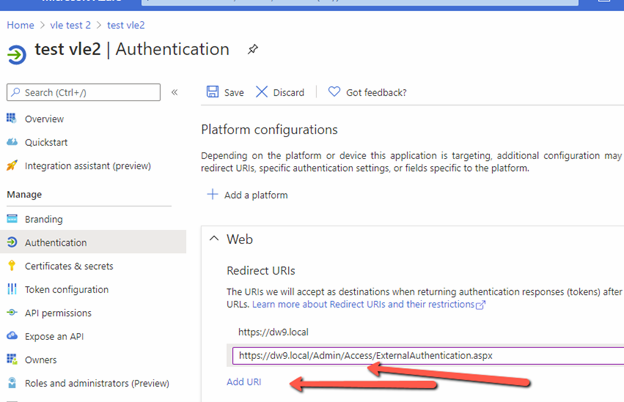
- For backend login you need to add https://[solution url]/Admin/Access/ExternalAuthentication.aspx – this is the URL which users must visit to login to backend with their Office 365 credentials
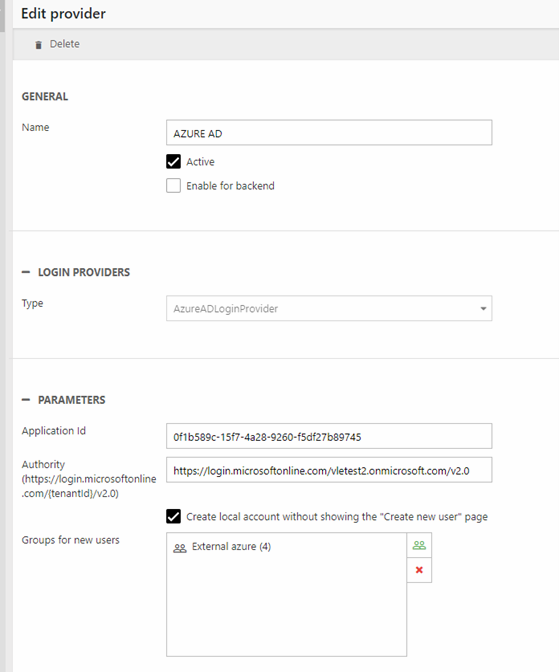
Set up Dynamicweb login provider
Once Azure AD is configured, you must login to the Dynamicweb solution and create an login provider for external authentication. You will need the two parameters from Azure AD which you were asked to save in the previous section:
- An Application ID
- The tenant ID/primary domain
Create the login provider:
- Go to Settings > Control Panel > External Authentication
- Click Add in the toolbar
- Select the AzureADLoginProvider and configure it:
- Under Application Id enter the application ID you saved during step 4
- Under Authority use the tenant id or primary domain in the url: https://login.microsoftonline.com/{tenantId|primarydomain}/v2.0
- If relevant, check the Create local account without showing the “Create new user” page checkbox and select a group for new users
- If relevant check the Enable for backend checkbox
- Save
- IIS reset
After this users from your Azure AD should be able to login to both frontend – using the regular login form on the website – and backend by visiting https://[solution url]/Admin/Access/ExternalAuthentication.aspx.